Some colleagues and customers call me a security freak because I question all products and deployments on about their protected mechanism. Security is not on my role list, but I simply cannot ignore it. It’s my on my IT-DNA 🙂
We all had training sessions and got tested at our companies for e-mail phishing, social engineering. It is required as it’s the most common attempt for network infiltration.
But what I’ve observed over my many years on the UCC area is the lack of security concerns regarding the other collaborations tools. They can be also used by to users … and more easier and quicker than an email phishing. It has the same attack vectors as e-mail phishing: Social engineering, sending instant messages with malicious links or attachments, …
Microsoft has done a impressive job and provides for MS365 customers several built-in protection mechanisms (for both identity and phishing) and many other security tools to keep your users protected as long as you have a well-trained security IT team to manage it. But what about the human-factor?
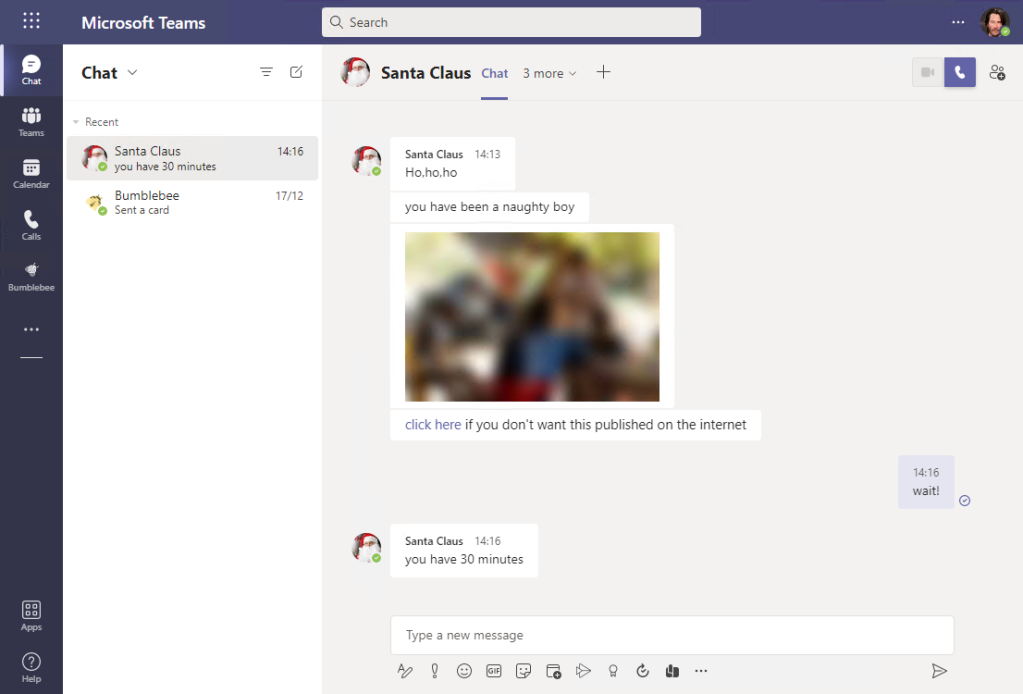
Using Teams to fish
The example is from Teams, but it can apply to other vendors. It’s simulated and not evolving any other persons than myself
The best way to explain my point is with an example and ‘hacker mindset’
- Create an Office365 demo tenant (it’s free)
- Go to LinkedIn, pick an IT company with Teams, look for some engineers with profile pictures
- Get the names of some of this company customer’s (usually the customer referrals, success stories
- Email addresses are easy to find or calculate (first name last name, company email domain name)
and confirm that the person exists and her display name, just by searching with your Teams client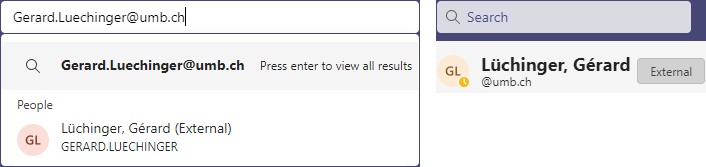
Skipping the details, we can create an user with the same display name on our ‘phishing tenant’. It’s now time to reach the victim.
Instant message method
Sending an internet link or an file might seem a suspicious approach, so let’s try social engineering by being the helpful support engineer (Luis Ramos AVENIQ) trying to help a customer’s user (RA):
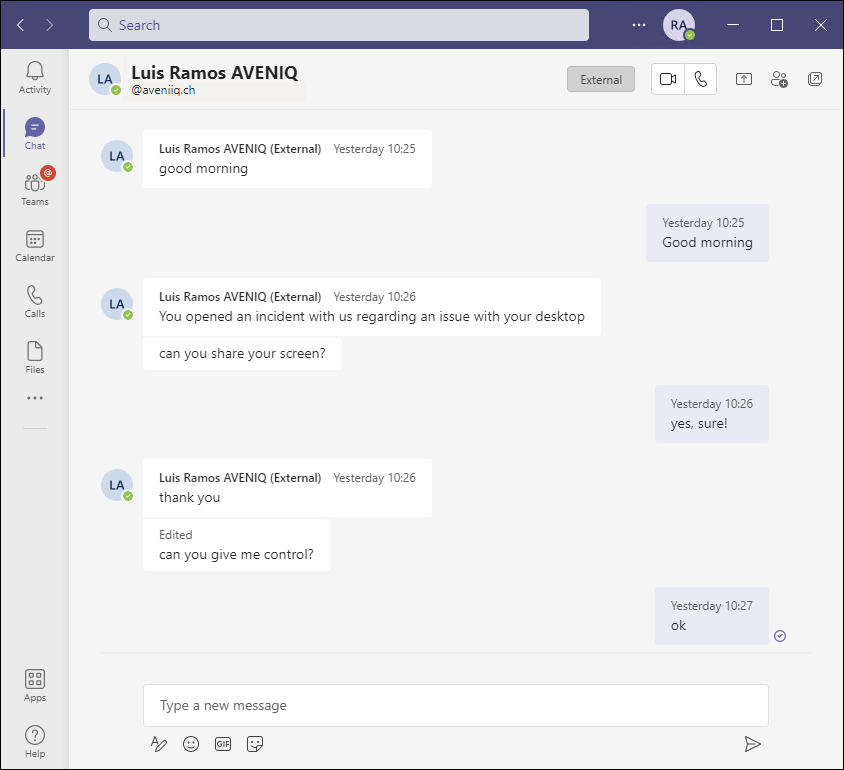
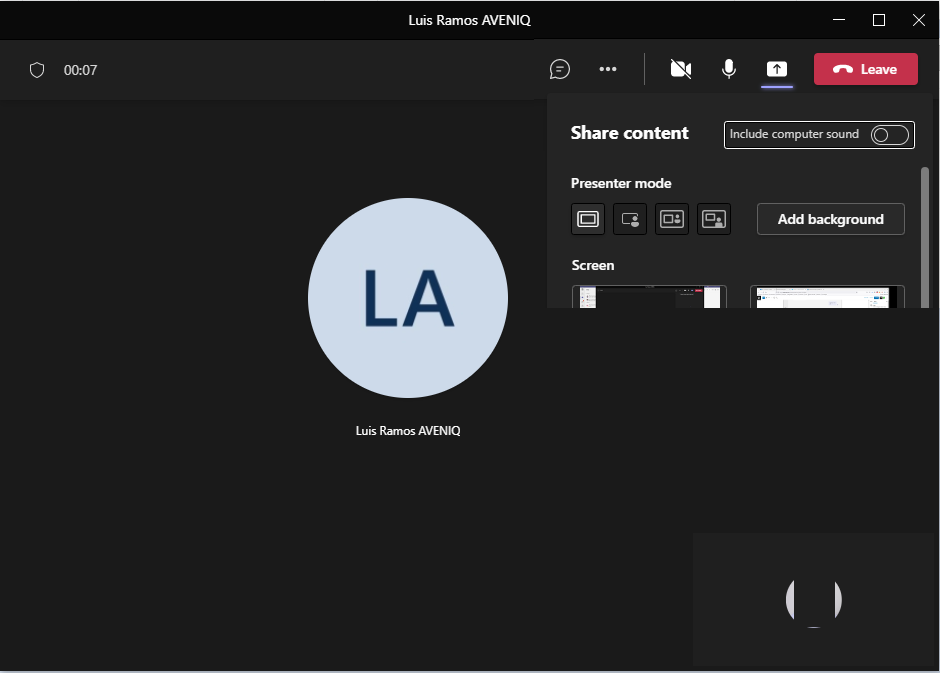
The external user has remote control of the user desktop. From this point now it’s up to your imagination.
On the above case, an attentive user can get suspicious if he’s paying attention to the aveniq.ch address.

But on the other hand, there are companies where the user email address (SMTP) doesn’t need to match his Teams address (SIP).
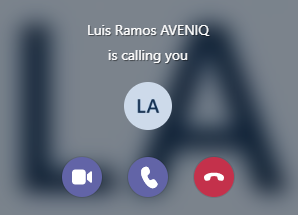
What about if we just call the user?
The incoming call toast notification will not help the user here:
And neither the main window, so now it’s up to the caller to convince the user:
Now the user needs to leave the mouse on the caller name to check if it’s really him!

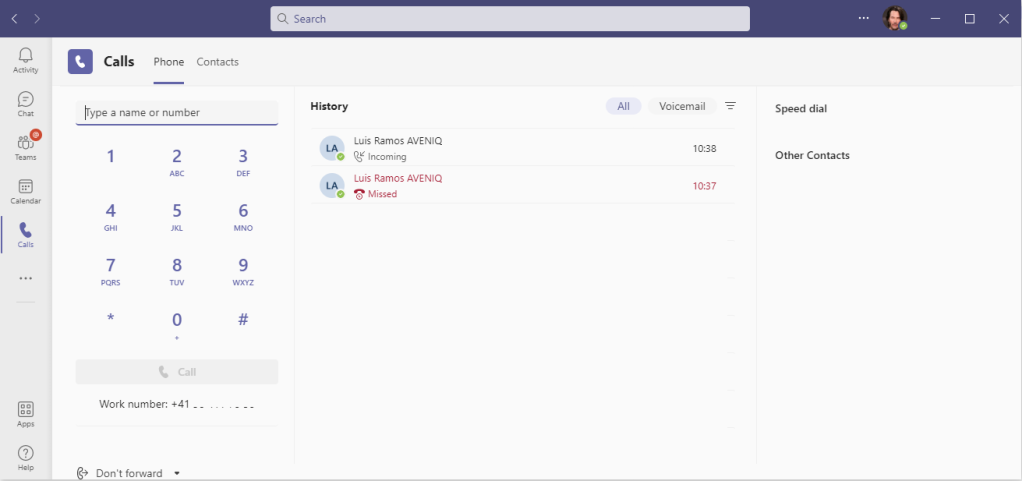
Another: the missed call phishing
You actually don’t need to try and wait for the user to answer. Teams will save a missed call with the name for the user be able to call you back 🙂
Final comments
- If by now you are thinking ‘I never thought of that, what should I do from now one?’
Then my post hit his goal 🙂 - Exploit success factor? depends on how tired and overwhelmed people are with confcalls, unread IM’s, homeoffice ‘burn-out’.
- Don’t get into the attitude: ‘never heard of such thing happening’ or “I will never fall for that!”
- This is an example of a social exploit
But hjust like any other software, Teams can also be vulnerable to technical exploits overtime. This one got out of the news radar: “We found a dangerous vulnerability in Microsoft Teams, but the company fixed it only after two months”
That’s it!
Have a Happy Christmas and don’t forget to write to Santa. He might have been watching you all year