Over the years of consulting services, managing and deploying UCC solutions, virtualization,… you might have thought several times about: why not provide them to all my customers from as a packed service?.
It’s nothing new nowadays – you called it ‘cloud’, hosting services, …

I’ve been planning and designing it for quite some years. So why not just share some memories, experience and concepts?
I decided to call it, since the 0 day, UCaaS – Unified Communications as a Service. Looks a cliché now, but it’s short and easy to catch 🙂 but also much broader than just providing Skype for Business
In this first part, I will just do a global overview that applies to any XaaS. I will focus on Lync/Skype4B on later posts.
Look at this one as a cooking lesson, starting by the main topic: the Kitchen 🙂
#1 It’s a service, so you need to see more then installing a couple of servers and connect the users! Before getting to that stage think, discuss and question about everything that comes to your mind.
Why? because we are about to run a business, any resource costs something and you need to count them on your selling price !
#2 We can go this way:
* buy a server, put on your basement or garage, connect to the internet, rent/create a webstore site and ready! (it can actually work)… or,
* everything below this line (more or less complex and as a existing company you might already have)
I like to group things to be easy to read and explain . Be aware that you might not need to own or have all on your side (you can just rent datacentre space, VM’s, backups).

 Base infrastructure
Base infrastructure
The ‘hardware’, where you place it and how you reach it: Servers, Storage, Backup robots, Switching, Routing, Firewalls, Load Balancers, Rack/Datacentre space, energy, internal and external connectivity (cabling, telecommunications, internet), …
By the way: all these also have something called ‘yearly maintenance costs’ if purchased and you will need to allocate some earnings to replacement them when it’s time.
if planning big, consider consulting Hardware providers that support ‘pay as you grow model’. Many of them have cloud-ready solutions from small footprint up to large scale (and you can find some nice surprises on less-known brands)
 Support infrastructure
Support infrastructure
Some invisible, but ‘must have’ systems:
- Virtualization- of course you will use it 🙂 and on this one we can even have mixed scenarios as the group above (virtual firewall, load balancers,…)
 Monitoring – Ever heard of an SLA ? if you are providing a service you will have to agree on an uptime. How can you measure and show to the customer? How can you detect failures or when you need more resources?
Monitoring – Ever heard of an SLA ? if you are providing a service you will have to agree on an uptime. How can you measure and show to the customer? How can you detect failures or when you need more resources?- Backup and DR – Are you ready to loose your data? what about the customers data?
 Security – you will need to manage patching and upgrades, antivirus, IDS, IPS… it’s a dangerous world outside, waiting to steal your customer data or take down you business.
Security – you will need to manage patching and upgrades, antivirus, IDS, IPS… it’s a dangerous world outside, waiting to steal your customer data or take down you business.
 Customer interfaces
Customer interfaces
This is your front porch and you should not hide it. If the prospective customers don’t like it, will they trust the inside of the housing?
- Customer infrastructure connectivity – the way that the customer systems and users will connect to your services. The simplest way is the internet, but it would require for some services, WAN, private networks and interoperability/integration solutions.
- The customer portal/tools – This can be from a simple status/account/billing view up to a self-provisioning, self-management
- Ticket / support handling – five customers might be easy to deal with phone calls and emails, but what about 30,100,…?
Software
I include on this section separately, because not everybody is aware of some legal aspects. Let’s take a look at Microsoft products: you cannot just buy a Windows license, install on your server and charge it to one (or more) customer(s) for a running service there.
Microsoft is clear on this: if you are a Hosting/Service Provider, you need to buy licensing throw a SPLA .
Like Microsoft, VMware and many other vendors provide (or enforce) this model and is not a bad option:
- The advantage is that it allows you to pay monthly for what you really use –
this is the pay-as-you-use model
- The inconvenient is that you need to report the usage periodically and allow auditing to your business
My advice is:
- as a Service Provider, contact the vendor and explain your intentions. They will help you to find the most profitable solution… most of the times.
- Don’t try to find ‘loopholes’…trust me: it will cost you much more later!
 Shared services
Shared services
Here you put all the platforms and services that can be shared between multiple.
Great examples are web servers hosting multiple websites. But pushing your skills to the limit, you can have a lot more. Multitenant solutions also would fit on this group.
Dedicated your best resources planning them! This is where your cost savings make a difference.
 Dedicated services
Dedicated services
This is what your best customers are looking and willing to pay for.
It’s your cash cow – the more you have here, the quicker your revenue increases. These business models have more opportunities, specially combined with standardized offers.
It has every group of systems serving unique customers:
- It should be a ‘block model’ – same deployment and standardized procedures, automation and self service tools, will keep operational costs low and predictable.
- But you can also include very ‘$pecific $olutions’ – these one gives you the opportunity to upsell consulting and managed services.
Skype for Business services model would fit on this group… but it might also fit for the group above? 😉
 Not there yet
Not there yet
If you already own a company then this is known to you: Work office place, furniture, energy, personal computers, HR, billing / account management, mobile devices, transportation/gas… you also pay for that, right
All done! What now?
 After joining and calculating all the pieces, test yourself doing at least these questions:
After joining and calculating all the pieces, test yourself doing at least these questions:
- What is the cost per service/per user? How much a VM with a specific size costs?
This is the lowest value will charge for your service.
=> Capitalism rule: to earn money you need to sell it for more than you pay for
- What is the break even point?
simulate, over and over the time! Be ready to answer: how many customers (or users) do you need to have to cover all the costs made so far?
Whomever is going to put money on this will make do that question before writing the checks (even yourself if you got the money)
- What is the ROI?
Investors, banks or stake holders will look for this (and many other tools).
If you need financing you need to promise when and how much will you pay back.
- Psychological one: are you an entrepreneur?
It needs investment analysis, financial control, technical know-how, purchasing/selling/negotiation skills, HR management, and so on. As the business creator you need deal with of them.
This will not be a one-man-show for long. Sooner or later you need help trust and delegate to others. Starting with someone it will look less difficult.
This might seem directed to start-ups guys, but it applies to existing companies. Product and/or Business developers need also to assume the above challenges, the problems, assume risks and responsibilities.
You are putting you neck and reputation on it and get ready to accept failure.
But of you planed all (not just a suicidal gambler), showed you the balls, and if successfully, the personal reward is priceless.
It’s still not over! there are some more strategic decisions for a go-to-market, on part 2 (writing in progress).









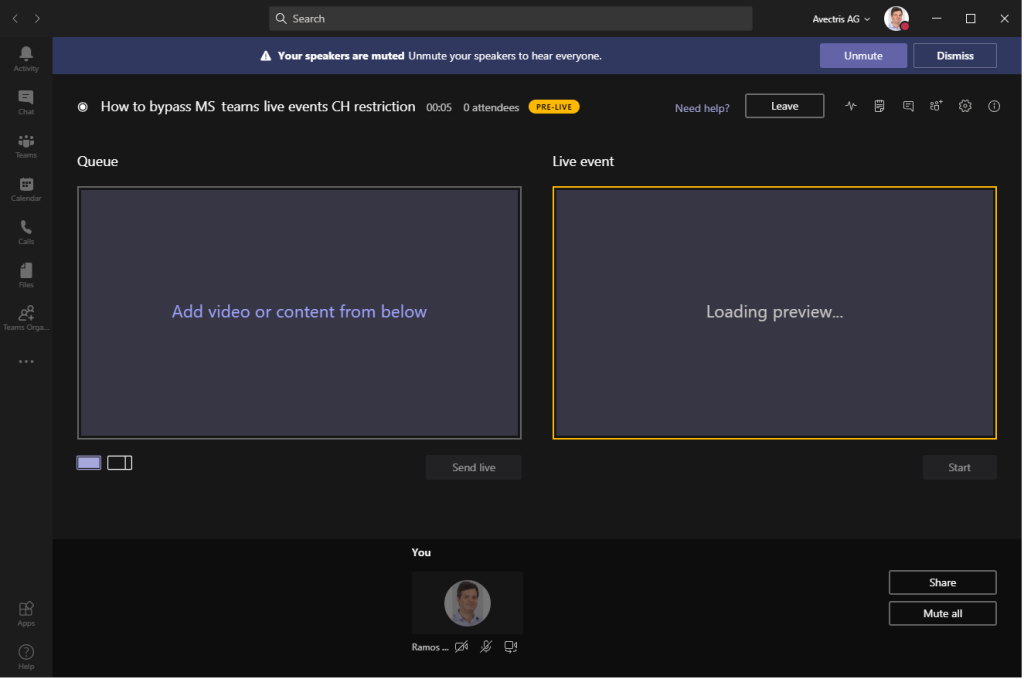



















 The Covid-19 pandemic caused an worldwide cause for concern. The best way to contain it is to reduce people direct interaction.
The Covid-19 pandemic caused an worldwide cause for concern. The best way to contain it is to reduce people direct interaction. Some companies have VPN policies (either to security reasons or simplified administration) to enforce all their managed PC to send all the traffic throw the VPN (let’s call it ‘Forced-tunnel VPN’).
Some companies have VPN policies (either to security reasons or simplified administration) to enforce all their managed PC to send all the traffic throw the VPN (let’s call it ‘Forced-tunnel VPN’).




























 Base infrastructure
Base infrastructure Support infrastructure
Support infrastructure Monitoring – Ever heard of an SLA ? if you are providing a service you will have to agree on an uptime. How can you measure and show to the customer? How can you detect failures or when you need more resources?
Monitoring – Ever heard of an SLA ? if you are providing a service you will have to agree on an uptime. How can you measure and show to the customer? How can you detect failures or when you need more resources? Security – you will need to manage patching and upgrades, antivirus, IDS, IPS… it’s a dangerous world outside, waiting to steal your customer data or take down you business.
Security – you will need to manage patching and upgrades, antivirus, IDS, IPS… it’s a dangerous world outside, waiting to steal your customer data or take down you business. Customer interfaces
Customer interfaces Shared services
Shared services Dedicated services
Dedicated services Not there yet
Not there yet After joining and calculating all the pieces, test yourself doing at least these questions:
After joining and calculating all the pieces, test yourself doing at least these questions:


